Face Recognition Access Control System is a relatively new biometric access control system based on advanced face, ID card, and fingerprint identification technologies. Being a split-system device, it consists of two separately configured portions: one for capturing images and receiving input information and the other for biometric identification and access control management. These features help increase the security and reliability of the system. Online data transmission is encrypted and the system can conduct remote control and management. It can be widely used in access control for banks, military, law enforcement agencies, and intelligent buildings.
| What is Biometrics? |
|
Biometrics are automated methods of recognizing a person based on a physiological or behavioral characteristic. Among the features measured are face, fingerprints, hand geometry, handwriting, iris, retinal, vein, and voice. Biometric data are separate and distinct from personal information. Biometric templates cannot be reverse-engineered to recreate personal information and they cannot be stolen and used to access personal information. Using a unique, physical attribute of your body, such as your fingerprint or iris, to effortlessly identify and verify that you are who you claim to be, is the best and easiest solution in the market today. That is the simple truth and power of Biometrics Technology today. Although biometric technology has been around for many years, modern advances in this emerging technology, coupled with big reductions in cost, now make biometrics readily available and affordable to consumers, small business owner, larger corporations and public sector agencies alike. |
| How Does a Fingerprint Optical Scanner Work? |
|
A fingerprint scanner system has two basic jobs -- it needs to get an image of your finger, and it needs to determine whether the pattern of ridges and valleys in this image matches the pattern of ridges and valleys in pre-scanned images. Only specific characteristics, which are unique to every fingerprint, are filtered and saved as an encrypted biometric key or mathematical representation. No image of a fingerprint is ever saved, only a series of numbers (a binary code), which is used for verification. The algorithm cannot be reconverted to an image, so no one can duplicate your fingerprints. 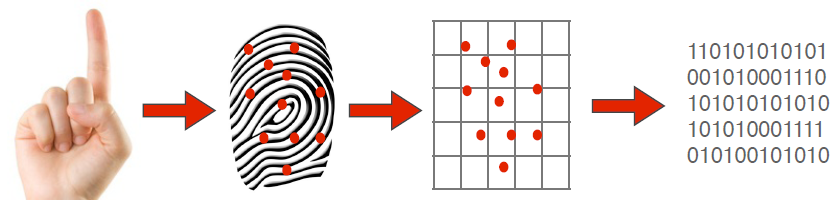 |
| Employees Privacy and Cleanliness Concerns? |
|
It is important to note that Easy Clocking’s biometric time clocks do not actually collect and store fingerprints. Instead, it saves a mathematical representation of the employee’s biometric data. When the biometric time clock scans a hand or finger during a supervised enrollment process, only an encrypted mathematical representation of the fingerprint is stored. As a result, it’s virtually impossible to duplicate the original image from that mathematical representation. Additionally, if employees question cleanliness, this concern should not be dismissed. Instead, you should assure employees that the time clock’s finger zone is not a hot zone for germs. In fact, it will be touched far less frequently than restroom door handles, water cooler spigots, or chairs in the break room. |
| Top Advantages of Fingerprint Authentication |
|
There are several ways an electronic time clock system can verify that somebody is who they say they are. Most systems are looking for one or more of the following:
· What you have
· Fingerprints are much harder to fake than identity cards. |
| Conclusion on Biometric & Workforce Management |
|
· Biometrics has been used effectively for more than a decade for time and attendance and workforce management. Despite widespread use, confusion and misconceptions about the technology and its capabilities persist. These concerns are easily dispelled when the facts about biometrics are established. |

• GPS310F Guard Patrol with GPRS
• GPS310 Guard Patrol with GPRS W
• GPS800 Guard Patrol with TFT sc
• GPS320 Guard Patrol/Tour Stick
• GPS500 Guard Patrol Stick with
• GPS500 Guard Patrol Stick with